Update: Misconfigured database breaches thousands of MedCall Advisors patient files
For the second time in one month, a researcher discovered North Carolina-based MedCall Healthcare Advisors has been leaking protected, personal data through a misconfigured Amazon S3 storage bucket.
WHAT HAPPENED
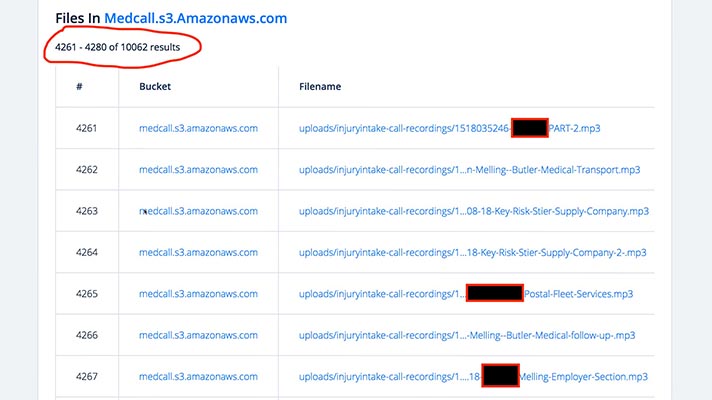
Security researcher Britton White contacted DataBreaches.net that MedCall, a workers compensation and healthcare solutions vendor, left a storage bucket containing 10,000 files exposed to the internet, available for download and or deletion or editing.
In fact, the database was listed on the searchable tool grayhatwarfare.com, which publicly lists current open Amazon S3 buckets.
Some patient names were included in filenames, and the database included names, email and postal addresses, phone numbers, dates of birth and Social Security numbers. Other files had recordings of patient evaluations and conversations with doctors, along with medications, allergies and other detailed personal health data.
What's worse is that this is the second time MedCall this database was exposed to the public in the past a month.
MedCall Founder and CEO Randy Baker spoke with Healthcare IT News to clarify just what happened. The database contents were from just one client. It's MedCall's policy to share files between clients using an FTP server, which is more secure and easier to monitor than a cloud storage bucket.
However, the client impacted by this exposed database did not want to set up the FTP server and insisted upon cloud storage, he explained.
"Being a startup, when you have a large new client, we try to accomodate," Baker said. "We should have pushed back... We've communicated with the client and locked everything down. They now understand what they have to do, and it will be done by the end of the day tomorrow."
"The lesson learned: Even though you may be a smaller company or startup, you may not recognize yourself as a viable target for people trying to compromise your data," he added. "Everyone is a potential target... It's a good wakeup call for us, I can assure you we'll be better focused on security going forward."
THE TREND
Security firm UpGuard’s Cyber Risk team discovered the first misconfiguration in mid-September. The detailed medical data for employees of 181 of the tech vendor’s 181 business locations and personally identifiable information for 3,000 people was exposed through an unsecured Amazon S3 storage bucket.
The leak of 7 gigabytes of data were PDF injury intake forms across MedCall’s 181 business locations, which included the descriptions of injuries and illnesses, along with records of phone calls between patients, MedCall operations and physicians.
There was also a directory of CSV files that included PII, complete with Social Security numbers for about 3,000 people enrolled in MedCall’s services.
There is no entry on the Department of Health and Human Services’ breach reporting tool for either of these breaches. While it’s uncertain if MedCall is covered under HIPAA, the patients involved in the breach should still be notified under state laws.
Under North Carolina law, businesses are required to report breaches to the Attorney General. But the state is still considering creating one of the strictest breach notification laws, which would require businesses to report a breach in just 15 days.
This story has been updated with comments from MedCall Healthcare Advisors CEO Randy Baker.
Focus on Cybersecurity
In October, we take a deep dive into security strategy and pressing threats.
Twitter: @JF_Davis_
Email the writer: jessica.davis@himssmedia.com























